Network Security and Data Communications
WTAMU CIDM-3385
Table of Contents:
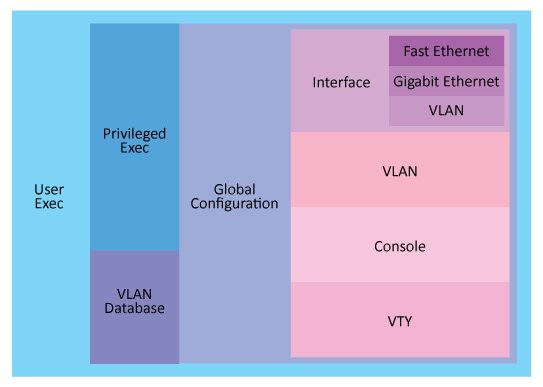
The OSI Model
The Open Systems Interconnection (OSI) model is a theoretical way of classifying and talking about the complex process of sending data on a network. You should be familiar with the OSI model because it is the most widely used method for understanding and talking about network communications. However, remember that it is only a theoretical model that defines standards for programmers and network administrators, not a model of actual physical layers.
OSI Model Benefits
The OSI model:
- Provides a common language and reference point for network professionals
- Divides networking tasks into logical layers for easier comprehension
- Allows specialization of features at different levels
- Aids in troubleshooting
- Promotes standards of interoperability between networks and devices
- Provides modularity in networking features (developers can change features without changing the entire approach)
OSI Model Limitations
However, you must remember the following limitations of the OSI model:
- OSI layers are theoretical and do not actually perform real functions.
- Industry implementations rarely have a layer-to-layer correspondence with the OSI layers.
- Different protocols are used within the OSI model to perform the different functions required to help send or receive the overall message. This can sometimes complicate the overall process.
- A particular protocol implementation may not represent every OSI layer (or may spread across multiple layers).
The following table compares the functions performed at each OSI model layer.
| Layer | Description and Keywords | |
| Application (Layer 7) |
The Application layer integrates network functionality into the host
operating system and enables communication between network clients
and services. The Application layer does not include specific
applications that provide services, but rather provides the
capability for services to operate on the network.
Most Application layer protocols operate at multiple layers down to the Session and even Transport layers. However, these protocols are classified as Application layer protocols because they start at the Application layer (the Application layer is the highest layer where they operate). Services typically associated with the Application layer include:
|
|
| Presentation (Layer 6) |
The Presentation layer formats, or presents, data in a compatible form
for receipt by the Application layer or the destination system.
Specifically, the Presentation layer ensures:
|
|
| Session (Layer 5) |
The Session layer manages the sessions in which data are transferred.
Session layer functions include:
|
|
| Transport (Layer 4) |
The Transport layer provides a transition between the upper and lower
layers of the OSI model, making the upper and lower layers
transparent from each other. Transport layer functions include:
|
|
| Network (Layer 3) |
The Network layer describes how data is routed across networks and on
to the destination. Network layer functions include:
|
|
| Data Link (Layer 2) | Logical Link Control (LLC) |
The Data Link layer defines the rules and procedures for hosts as they
access the Physical layer. These rules and procedures define:
|
| Media Access Control (MAC) | ||
| Physical (Layer 1) |
The Physical layer of the OSI model sets standards for sending and
receiving electrical signals between devices. Protocols at the
Physical layer identify:
|
|
TCP/IP Model Layers
The TCP/IP model incorporates the general concepts and structure of the OSI model. The layers of the TCP/IP model are as follows:
| Layer | Description |
| Application | The Application layer corresponds to the Session, Presentation, and Application layers of the OSI model. Protocols associated with the Application layer include FTP, HTTP, Telnet, SMTP, DNS, and SNMP. |
| Host-to-Host | The Host-to-Host layer is comparable to the Transport layer of the OSI model. It is responsible for error checking and reliable packet delivery. Here, the data stream is broken into segments that must be assigned sequence numbers so they can be reassembled correctly on the remote side after they are transported. Protocols associated with the Host-to-Host layer include Transport Control Protocol (TCP) and User Datagram Protocol (UDP). |
| Internet | The Internet layer is comparable to the Network layer of the OSI model. It is responsible for moving packets through a network. This involves addressing hosts and making routing decisions to identify how the packet traverses the network. Protocols associated with the Internet layer include Address Resolution Protocol (ARP), Internet Control Message Protocol (ICMP), and the Internet Group Management Protocol (IGMP). |
| Network Access | The Network Access layer corresponds to the Physical and Data Link layers of the OSI model. It is responsible for describing the physical layout of the network and formatting messages on the transmission medium. |
The TCP/IP model focuses specifically on the functions in the Internet layer and Host-to-Host layers. All other functions of the traditional OSI model are encompassed in the first and fourth layers.
Mnemonic Device For Layers
To help remember the layer names of the OSI model, try the following mnemonic devices:
| Layer | Name | Mnemonic (Bottom to top) |
Mnemonic (Top to bottom) |
| Layer 7 | Application | Away | All |
| Layer 6 | Presentation | Pizza | People |
| Layer 5 | Session | Sausage | Seem |
| Layer 4 | Transport | Throw | To |
| Layer 3 | Network | Not | Need |
| Layer 2 | Data Link | Do | Data |
| Layer 1 | Physical | Please | Processing |
Have some fun and come up with your own mnemonic for the OSI model, but stick to one so you don't get confused.
Chapter 5 IP Addressing
Back to top
As you study this section, answer the following questions:
- What is an octet?
- What is the decimal equivalent of the following binary number? 01100111. What is the binary equivalent of the following decimal number? 211.
- How is the network portion of an IP address identified?
- Which portion of a class C address designates the network address?
- What is the difference between subnetting and supernetting? Which method uses a subnet mask that is longer than the default subnet mask?
- What does /14 mean in the following IP address: 199.78.11.12/14?
- How does variable-length subnet masking work?
In this section, you will learn to:
- Configure IP addresses.
- Configure IP addresses on mobile devices.
The key terms for this section include:
| Term | Definition |
| IANA | The Internet Assigned Numbers Authority is a function of a nonprofit private American corporation that oversees global IP address allocation, autonomous system number allocation, root zone management in the Domain Name System, media types, and other Internet Protocol-related symbols and internet numbers. |
| Classful IP Addresses |
Classful addresses are IP addresses that use a default subnet mask, as follows:
|
| VLSM | Variable Length Subnet Masking (VLSM) is the method used to divide an IP address into subnets of different sizes. When using VLSM, you ignore the default subnet mask boundaries and specify a custom number of subnet mask bits. |
| Subnetting | The process of dividing a large network into smaller networks. |
| Supernetting | The process of combining two or more networks. |
| Classless Inter-Domain Routing (CIDR) |
A set of internet protocol standards used to create unique identifiers for networks and host devices. |
| ANDing | The process used to determine the network address/ID. |
| Subnet Mask | A 32-bit number that defines which portion of an IPv4 address identifies the network address and which portion of the address defines the host address. |
| Network ID | A 32-bit number that identifies the network an IPv4 address belongs to. |
IP Addresses
IP addresses allow hosts to participate on IP-based networks. The following are important things to know about IP addresses:
- An IP address is a 32-bit binary number represented as four octets (four 8-bit-numbers). Each octet is separated by a period.
- IP addresses can be represented two different ways:
- Decimal (e.g., 131.107.2.200). In decimal notation, each octet must be between 0 and 255.
- Binary (e.g., 10000011.01101011.00000010.11001000). In binary notation, each octet is an 8-character number.
- To convert from binary to decimal, memorize the decimal equivalent to
the following binary numbers:
Add together the decimal values of each bit position with a 1 value. For example, the decimal equivalent of 10010101 is:10000000 01000000 00100000 00010000 00001000 00000100 00000010 00000001 128 64 32 16 8 4 2 1
128 + 16 + 4 + 1 = 149 - The IP address includes both the network and the host address.
- A subnet mask is a 32-bit number associated with an IP address that identifies the network portion of the address. In binary form, the subnet mask is always a series of 1s followed by a series of 0s (1s and 0s are never mixed in sequence in the mask). A simple mask might be 255.255.255.0 (i.e., 11111111.11111111.11111111.00000000).
- IP addresses have a default class. The address class identifies
the range of IP addresses and the default subnet mask used for the range.
The following table shows the default address class for each IP address
range:
Class Address Range First Octet Range Default Subnet Mask A 1.0.0.0 to 126.255.255.255 1–126
(00000001–01111110 binary)255.0.0.0 B 128.0.0.0 to 191.255.255.255 128–191
(10000000–10111111 binary)255.255.0.0 C 192.0.0.0 to 223.255.255.255 192–223
(11000000–11011111 binary)255.255.255.0 D 224.0.0.0 to 239.255.255.255 224–239
(11100000–11101111 binary)n/a E 240.0.0.0 to 255.255.255.255 240–255
(11110000–11111111 binary)n/a - When using the default subnet mask for an IP address, you have the
following number of subnet addresses and hosts per subnet:
- There are only 126 Class A network IDs (most of these addresses are already assigned). Each class A address gives you 16,777,214 hosts per network.
- There are 16,384 Class B network IDs. Each class B address gives you 65,534 hosts per network.
- There are 2,097,152 Class C network IDs. Each class C address gives you 254 hosts per network.
- Class D addresses are used for multicast groups rather than network and host IDs.
- Class E addresses are reserved for experimental use.
Special Considerations
As you are assigning IP addresses to hosts, think of the following special considerations:
| Address | Consideration |
| Network |
The first address in an address range is used to identify the network
itself. For the network address, the host portion of the address
contains all 0s. For example:
|
| Broadcast |
The last address in the range is the broadcast address, and it is used
to send messages to all hosts on the network. In binary form, the
broadcast address has all 1s in the host portion of the address. For
example, assuming the default subnet masks are used:
The broadcast address might also be designated by setting each of the network address bits to 0. For example, 0.0.255.255 is the broadcast address of a Class B address. This designation means "the broadcast address for this network." |
| Host Addresses |
When you are assigning IP addresses to hosts, understand the
following:
Another way to identify a host on a network is to set the network portion of the address to all 0s. For example, the address 0.0.64.128 means "host 64.128 on this network." |
| Local Host | Addresses in the 127.0.0.0 range are reserved to refer to the local host (the host you're currently working at). The most commonly used address is 127.0.0.1, which is the loopback address. |
Because IP addresses assigned to hosts must be unique, the use of IP addresses on the internet is controlled by organizations that ensure that every organization is given its own range of IP addresses to assign to hosts:
- The Internet Assigned Numbers Authority (IANA) manages the assignment of IP addresses on the internet. IANA is operated by the Internet Corporation for Assigned Names and Numbers (ICANN).
- IANA allocates blocks of IP addresses to Regional Internet Registries (RIRs). An RIR has authority over IP addresses in a specific region of the world.
- An RIR assigns blocks of addresses to Internet Service Providers (ISPs).
- An ISP assigns one or more IP addresses to individual computers or organizations connected to the Internet.
</br>
Subnetting
Subnetting is the process of dividing a large network into smaller networks called subnets. When you subnet a network, each network segment has a different network address, or subnet address. In practice, the terms network and subnet are used interchangeably to describe a physical network segment with a unique network address.
Functions of Subnetting
From a physical standpoint, subnetting is necessary because network architectures impose a limit on the number of hosts allowed on a single network segment. As your network grows, you will need to create subnets (physical networks) to:
- Increase the number of devices that can be added to the LAN (to overcome the architecture limits)
- Decrease the number of devices on a single subnet (to reduce traffic congestion)
- Reduce the processing load placed on computers and routers
- Isolate sensitive systems on the network
Subnetting is also used to efficiently allocate available IP addresses. For example, an organization with a class B network ID is allocated enough addresses for 65,536 hosts. However, if the organization in practice uses only 10,000 of those host IDs, over 55,000 IP addresses are going unused. Subnetting provides a way to break the single class B network ID into multiple smaller network IDs.
- Subnetting uses custom subnet masks instead of the default subnet masks (e.g., using 255.255.255.0 with a Class B address instead of the default 255.255.0.0).
- When you subnet a network by using a custom mask, you can divide the IP addresses between several subnets. However, you also reduce the number of hosts available on each network.
- Using custom subnet masks is often called classless addressing because the subnet mask cannot be inferred simply from the class of a given IP address. The address class is ignored, and the mask is always supplied to identify the network and host portions of the address.
The following table shows how a Class B address can be subnetted to provide additional subnet addresses. Notice that by using a custom subnet mask, the Class B address looks like a Class C address.
Subnetting Class B Addresses
| Default Example | Custom Example | |
| Network Address | 188.50.0.0 | 188.50.0.0 |
| Subnet Mask | 255.255.0.0 | 255.255.255.0 |
| # of Subnet Addresses | One | 254 |
| # of Hosts per Subnet | 65,534 | 254 per subnet |
| Subnet Address(es) | 188.50.0.0 (only one) | 188.50.1.0 188.50.2.0 188.50.3.0 (and so on) |
| Host Address Range(s) | 188.50.0.1 to 188.50.255.254 | 188.50.1.1 to 188.50.1.254 188.50.2.1 to 188.50.2.254 188.50.3.1 to 188.50.3.254 (and so on) |
Remember that the last valid host address ends with 254 because 255 is a broadcast address and is not available as a host address. For example:
- For the class A network address 115.0.0.0, the host range is 115.0.0.1 to 115.255.255.254.
- For the class B network address 154.90.0.0, the host range is 154.90.0.1 to 154.90.255.254.
- For the class C network address 221.65.244.0, the host range is 221.65.244.1 to 221.65.244.254.
While subnetting divides a large address space into multiple subnets, supernetting combines multiple small network addresses into a single larger network. Supernetting allows multiple Class C addresses to be combined into a single network.
Variable Length Subnet Masking (VLSM)
Classful IP Addresses
Classful addresses are IP addresses that use a default subnet mask, as follows:
- Class A: 255.0.0.0
- Class B: 255.255.0.0
- Class C: 255.255.255.0
They are considered classful because the default subnet mask identifies the network portion and host portion of the IP address.
Classless IP Addresses
Classless addresses, on the other hand, use a custom mask value to separate the network and host portions of the IP address. Classless addressing is made possible using Classless Inter-Domain Routing (CIDR). CIDR allows you to use only part of an octet for the network address. This is called partial subnetting, or variable-length subnet masking (VLSM).
VLSM - Variable Length Subnet Masking
When using VLSM, you ignore the default subnet mask boundaries and specify a custom number of subnet mask bits. For example, you could define a subnet mask of 255.255.252.0. In addition to the first and second octets, this mask also assigns the first six bits in the third octet to be used for the network portion of the address. This mask would appear in binary notation as follows:
11111111.11111111.11111100.00000000
As you can see, the six bits are reallocated from the host address to the network address. This allows you to create additional subnets, but it reduces the number of host addresses available within each one.
For example, suppose your network is composed of four separate physical network segments connected by routers. The network uses the 10.0.0.0 private IP addressing scheme, but you want to divide the 10.0.0.0 network into four separate subnets. Under classful addressing, this network would use the first octet for the network address and the last three octets for node addresses. However you need to divide this large network into four subnets. To do this, you need to reconfigure the subnet mask to include the first two bits of the second octet, creating four additional networks. Instead of using the default Class A subnet mask of 11111111.00000000.00000000.00000000 (255.0.0.0), you use a subnet mask of 11111111.11000000.00000000.00000000 (255.192.0.0). Using CIDR notation, you can specify a prefix of /10 to indicate you are using 10 bits for the subnet mask.
The following are four possible values in the IP address for the two extra bits that have been added to the subnet mask:
- 00 = 0
- 01 = 64
- 10 = 128
- 11 = 192
These values define the lower and upper boundaries for the four subnets created by the classless subnet mask, as shown in the following table:
| Subnet Address | Subnet Mask | Subnet Host Address Range | Subnet Broadcast Address |
| 10.0.0.0 | 255.192.0.0 | 10.0.0.1–10.63.255.254 | 10.63.255.255 |
| 10.64.0.0 | 255.192.0.0 | 10.64.0.1–10.127.255.254 | 10.127.255.255 |
| 10.128.0.0 | 255.192.0.0 | 10.128.0.1–10.191.255.254 | 10.191.255.255 |
| 10.192.0.0 | 255.192.0.0 | 10.192.0.1–10.255.255.254 | 10.255.255.255 |
On the internet, you can access many subnet calculators to calculate subnet boundaries, host addresses, and broadcast addresses.
IP Address Assignment
The following table lists several options for assigning IP addresses.
| Method | Uses |
| Dynamic Host Configuration Protocol (DHCP) |
A DHCP server is a special server configured to pass out IP addresses
and other IP configuration information to network clients. DHCP
servers ensure that each client is assigned a unique IP address.
DHCP is the preferred IP configuration method for small, medium, and large networks. |
| Static (Manual) Assignment |
Static addressing means that IP configuration information is manually configured on each host. Static addressing is best
used in the following situations:
Static addressing is very susceptible to configuration errors and duplicate IP address configuration errors. Static addressing disables both APIPA and DHCP functions on the host. |
APIPA and Alternate IP Addressing
As you study this section, answer the following questions:
- How do you know if a host is using an APIPA address?
- Which IP configuration parameters are set when APIPA is used? Which parameters are not set?
- In which scenarios would an alternate IP configuration simplify IP configuration?
In this section, you will learn to:
- Set Up alternate addressing.
- Configure alternate addressing.
The key terms for this section include:
| Term | Definition |
| Automatic Private IP Addressing (APIPA) | APIPA provides an option for automatic IP address assignment without a DHCP server. APIPA is enabled by default on most modern operating systems, including Windows and Linux. |
| Alternate IP Configuration | A manual configuration of a computer's IP address, default gateway, DNS server address, and WINS address. This configuration is used if the DHCP server fails to provide this similar information. |
If a host is configured to obtain its IP address from a DHCP server but that server is unreachable, then an alternate IP address assignment method may be employed as follows:
| Method | Description |
| Automatic Private IP Addressing (APIPA) |
APIPA provides an option for automatic IP address assignment without a
DHCP server. APIPA is enabled by default on most modern operating
systems, including Windows and Linux.
Using APIPA, hosts can assign themselves an IP address on the 169.254.0.0 network (with a mask of 255.255.0.0) if they can't locate a DHCP server. If a network host is configured to use dynamic IP addressing and a DHCP server can't be contacted, APIPA assigns a temporary IP address to the host. However, only the IP address and mask are assigned. Default gateway and DNS server addresses are not assigned. For this reason, APIPA can be used only to enable communications within a single subnet. Communication with other networks, including the internet, are not possible. In addition, communication with network infrastructure devices that use static IP addressing, such as servers, is not possible even if they are on the same local subnet as the APIPA host. |
| Alternate IP Configuration | With an alternate IP configuration, static IP configuration values are used if a DHCP server cannot be contacted. When you configure an alternate IP address, APIPA is automatically disabled. It is recommended that you use an IP configuration other than APIPA because you hosts need to access other systems on the local subnet and on other networks, including the internet. Alternate IP configuration also allows continued access to servers and other network infrastructure devices that use static IP addresses. |
DHCP Server Configuration
As you study this section, answer the following questions:
- What type of configuration parameters can be delivered using DHCP?
- What are the advantages of static IP address assignments?
- When might you want to use static IP addressing?
In this section, you will learn to:
- Configure a DHCP server.
- Configure DHCP options.
- Create DHCP exclusions.
- Create DHCP client reservations.
- Configure a DHCP client.
The key terms for this section include:
| Term | Definition |
| DHCP Discover (D) | The client begins by sending out a DHCP Discover frame to identify DHCP servers on the network. |
| DHCP Offer (O) | A DHCP server that receives a Discover request from a client responds with a DHCP Offer advertisement, which contains an available IP address. If more than one DHCP server responds with an offer, the client usually responds to the first offer it receives. |
| DHCP Request (R) | The client accepts the offered IP address by sending a DHCP request back to the DHCP server. |
| DHCP ACK (A) | The DHCP server responds to the request by sending a DHCP ACK (acknowledgement). At this point, the IP address is leased to and configured on the DHCP client. |
The dynamic host configuration protocol (DHCP) centralizes management of IP addressing in a network by allowing a server to dynamically assign IP addresses to clients. DHCP also allows mobile users, who move from network to network, to easily obtain an IP address appropriate for each network they connect to.
Obtain an Address from a DHCP Server
Because a DHCP client doesn't have an IP address when it initially boots, it must use broadcast frames to communicate with a DHCP server. The table below describes the method used to obtain an address from a DHCP server.
| Broadcast | Description |
| DHCP Discover (D) | The client begins by sending out a DHCP Discover frame to identify DHCP servers on the network. |
| DHCP Offer (O) | A DHCP server that receives a Discover request from a client responds with a DHCP Offer advertisement, which contains an available IP address. If more than one DHCP server responds with an offer, the client usually responds to the first offer that it receives. |
| DHCP Request (R) | The client accepts the offered address by sending a DHCP request back to the DHCP server. If multiple offers were sent, the DHCP request message from the client also informs the other DHCP servers that their offers were not accepted and the IP addresses contained in their offers can be made available to other clients. |
| DHCP ACK (A) | The DHCP server responds to the request by sending a DHCP ACK (acknowledgement). At this point, the IP address is leased to and configured on the DHCP client. |
If the DHCP server is on a different subnet, additional configuration steps are required, since network routers drop the DHCP broadcast frames by default.
Configuring a DHCP Server
Keep in mind the following when configuring a DHCP Server:
- The DHCP service needs to auto-start when the server boots.
- The server must have a static IP address.
- A MAC reservation is an association of a MAC address with a specific IP address. In other words, the client with the specified MAC address is assigned the same IP address each time it requests an address.
- An IP reservation means you program MAC addresses into the DHCP server. When the DHCP server sees a certain host requesting an IP address based on its MAC, it will give you a specific IP address.
For a DHCP server to deliver IP addresses, it must have a scope configured. A scope is the range of IP addresses that the DHCP server can assign to clients. A scope can also be called a pool. When working with scopes, remember the following:
- There should be only one scope per network segment.
- The scope must be activated before the DHCP server can assign addresses to clients. After you activate a scope, you should not change it.
- A scope has a subnet mask that determines the subnet for a given IP address. You cannot change the subnet mask of an existing DHCP scope; to change the subnet mask used by a scope, you must delete and recreate the scope.
- Lease duration values are part of the scope properties, and they determine the length of time a client can use an IP address leased through DHCP.
The DHCP server can also be configured with exclusions, which are specific addresses in the range that should not be assigned.
DHCP Server Functions
In addition to providing IP addresses, a DHCP server can also provide clients with additional IP configuration parameters using options. Commonly used DHCP options include the subnet mask, the default gateway address, and a DNS server address. The following levels of options can be configured:
- Server options are applied to all computers that get an IP address from the DHCP server, regardless of which scope they obtain the address from (for example, if your organization has only one DNS server, then all DHCP clients need the same DNS server address.)
- Scope options are applied to all computers that get an IP address from a particular scope on the DHCP server (for example, because scopes are associated with specific subnets, each scope needs to be configured with the appropriate default gateway address option.)
- Client options are applied to a specific DHCP client. The client's MAC address is used to identify which system receives the option.
The DHCP console provides context-sensitive icons to reflect DHCP server status as follows:
- A check mark in a green circle indicates that the DHCP server is connected and authorized.
- A red down arrow indicates that the DHCP server is connected, but not authorized.
- A horizontal white line inside a red circle indicates that the DHCP server is connected, but the current user does not have the administrative credentials necessary to manage the server.
- An exclamation point inside a yellow triangle indicates that 90% of available addresses for server scopes are either in use or leased.
- An exclamation point inside a blue circle indicates that 100% of available addresses for server scopes are either in use or leased.
DHCP Relay
As you study this section, answer the following questions:
- What is the difference between an RFC 1542 compliant router and a DHCP relay agent?
In this section, you will learn to:
- Configure a DHCP relay agent
- Add a DHCP server on another subnet
The key terms for this section include:
| Term | Definition |
| RFC 1542 Compliant Router | An RFC 1542 compliant router listens for DHCP traffic and routes any received DHCP frames to the appropriate subnet. . |
| DHCP Relay Agent | A function of the Routing and Remote Access service (RRAS) role on a Windows server, the DHCP Relay Agent service sends the DHCP packets it receives to a remote DHCP server on a different subnet. |
Because a DHCP client doesn't have an IP address assigned when it initially boots, it must use broadcast frames to communicate with a DHCP server. If the server is on a different subnet than the client, then the DHCP requests sent by the client will not reach the server because broadcast frames are dropped by network routers. If your network is configured in this manner, you can implement one of the following mechanisms to forward DHCP broadcasts through network routers to a remote DHCP server on a different subnet:
| Option | Description |
| RFC 1542 Compliant Router |
An RFC 1542 compliant router listens for DHCP traffic and routes any
received DHCP frames to the appropriate subnet. For example, on a Cisco
router, you can enable this functionality by using the ip
helper-address command. The syntax is:
ip helper-address [server_address]Replace [server_address] with the IP address of the remote DHCP server. |
| DHCP Relay Agent |
If you use a Windows server in your network, then you can install the
Routing and Remote Access service (RRAS) role on the server and enable
the DHCP Relay Agent Role service. The DHCP Relay Agent service sends
the DHCP packets it receives to a remote DHCP server on a different
subnet. To configure the DHCP Relay service, you must:
|
DNS Name Resolution
As you study this section, answer the following questions:
- How are host names organized in DNS?
- What is the difference between a forward lookup zone and a reverse lookup?
- What is the role of the root servers in DNS?
- In DNS, what is the difference between a zone and a domain?
- What is the difference between an A record and a PTR record?
In this section, you will learn to:
- Configure DNS addresses.
- Create standard DNS zones.
- Create reverse DNS zones.
- Create host records.
- Create CNAME records.
- Troubleshoot DNS records.
The key terms for this section include:
| Term | Definition |
| . (dot) domain | The . (dot) domain, or root domain, denotes a fully qualified, unambiguous domain name. |
| Top-Level Domain (TDL) |
The last part of a domain name (for example, .com, .edu, .gov). TDLs are managed by the Internet Corporation of Assigned Names and Numbers (ICANN). |
| Fully Qualified Domain Name (FQDN) |
The host name and all domain names separated by periods. The final period (which is for the root domain) is often omitted and only implied. |
| Additional Domains | Additional domains are second-level domains with names registered to an individual or organization for use on the internet. These names are based on an appropriate top-level domains, depending on the type of organization or geographic location where a name is used. Yahoo.com and microsoft.com are examples of additional domains in your DNS structure. |
| Hostname | The hostname is the part of a domain name that represents a specific host. For example, "www" is the hostname of www.example.com. |
| Records | Records are used to store entries for hostnames, IP addresses, and other information in the zone database. Each host has at least one record in the DNS database that maps the hostname to the IP address. |
| Authoritative Server | An authoritative server is a DNS server that has a complete copy of all the records for a particular domain. |
| Dynamic DNS (DDNS) |
DDNS enables clients or the DHCP server to update records in the zone database. Without dynamic updates, all A (host) and PTR (pointer) records must be configured manually. With dynamic updates, host records are created and deleted automatically whenever the DHCP server creates or releases an IP address lease. |
The Domain Name System (DNS) is a hierarchical distributed database that maps logical host names to IP addresses. DNS is a distributed database because no one server holds all of the DNS information. Instead, multiple servers hold portions of the data as follows:
- Each division of the database is held in a zone database file.
- Zones typically contain one or more domains, although additional servers might hold information for child domains.
- DNS servers hold zone files and process name resolution requests from
client systems.
Parts
of a DNS
The DNS is made up of the following components:
| Component | Description |
| . (dot) domain | The . (dot) domain, or root domain, denotes a fully qualified, unambiguous domain name. |
| Top-Level Domain (TLD) | A TLD is the last part of a domain name (for example, .com, .edu, .gov). TLDs are managed by the Internet Corporation of Assigned Names and Numbers (ICANN). |
| Fully Qualified Domain Name (FQDN) | The FQDN includes the host name and all domain names separated by periods. The final period (which is for the root domain) is often omitted and only implied. |
| Additional Domains (Second-Level Domains) |
Additional domains are second-level domains with names registered to an individual or organization for use on the internet. These names are based on an appropriate top-level domain, depending on the type of organization or geographic location where a name is used. Yahoo.com and microsoft.com are examples of additional domains in your DNS structure. |
| Host Name | The host name is the part of a domain name that represents a specific host. For example, "www" is the host name of www.example.com. |
| Records |
Records are used to store entries for host names, IP addresses,
and other information in the zone database. Each host has at least
one record in the DNS database that maps the host name to the IP
address. Common resource records include:
|
| Authoritative Server | An authoritative server is a DNS server that has a complete copy of all the records for a particular domain. |
| Dynamic DNS (DDNS) |
DDNS enables clients or the DHCP server to update records in the zone
database. Without dynamic updates, all A (host) and PTR (pointer)
records must be configured manually. With dynamic updates, host
records are created and deleted automatically whenever the DHCP
server creates or releases an IP address lease. Dynamic updates
occur when:
|
Recursion Process
When you use the host name of a computer (for example, if you type a URL
such as www.mydomain.com), recursion is employed to find the IP address.
Recursion is the process by which a DNS server uses root name servers
and other DNS servers to perform name resolution. The following steps occur:
- The host looks in its local cache to see if it has recently resolved the host name.
- If the information is not in the cache, it checks the Hosts file. The Hosts file is a static text file that contains host-name-to-IP address mappings.
- If the IP address is not found, the host contacts its preferred DNS server. If the preferred DNS server can't be contacted, the host continues contacting additional DNS servers until one responds.
- The host sends the name information to the DNS server. The DNS server checks its cache and Hosts file. If the information is not found, the DNS server checks any zone files that it holds for the requested name.
- If the DNS server can't find the name in its zones, it forwards the request to a root zone name server. This server returns the IP address of a DNS server that has information for the corresponding top-level domain (such as .com).
- The first DNS server requests the information from the top-level domain server. The server returns the address of a DNS server with the information for the next highest domain. This process continues until a DNS server is contacted that holds the necessary information.
- The DNS server places the information in its cache and returns the IP address to the client host. The client host also places the information in its cache and uses the IP address to contact the desired destination device.
DNS Facts
The following are some additional facts about DNS:
- A forward lookup finds the IP address for a given host name. A reverse lookup finds the host name from a given IP address.
- Root DNS servers hold information for the root zone ( . ). Root servers answer name resolution requests by supplying the address of the corresponding top-level DNS server (servers authoritative for .com, .edu, and similar domains).
- On very small networks, you could configure a HOSTS file with several entries to provide limited name resolution services. However, you would have to copy the HOSTS file to each client. The work involved in this solution is only suitable for temporary testing purposes or for overriding information that might be received from a DNS server.
- On the client, you should configure a list of DNS suffixes you want to
append to unqualified DNS names submitted by clients for resolution as
follows:
- Configure a single DNS suffix for clients using a DHCP option on the DHCP server.
- Configure multiple suffixes by adding them to the client manually.
IPV-6
As you study this section, answer the following questions:
- What is the primary reason for developing IPv6?
- How many hexadecimal numbers are in an IPv6 address? How does this compare to a MAC address?
- What do you add to an IPv6 address when you remove one or more quartets with all 0s?
- What information is included within the IPv6 address prefix?
- How many numbers are used for the interface ID? How can the interface ID be related to the MAC address?
- What is the difference between ISATAP and 6to4 tunneling?
- What is the difference between stateful autoconfiguration and stateless autoconfiguration?
In this section, you will learn to:
- Configure IPv6 addresses.
- Configure a DHCP6 server.
- Configure an IPv6 address.
The key terms for this section include:
| Term | Definition |
| Global-Unicast | An IPv6 address type that is publicly routable and can be used in the internet. |
| Unique-Local | An IPv6 address type that indicates an IP address is a private IP address. |
| Link-Local | An IPv6 address type that indicates that the IP address was configured by default. |
| Multicast | An IPv6 address type that indicates that the packet is addressed to a number of hosts on the network, but not all hosts. |
| Prefix ID | The leftmost bits of the IPv6 address, also know as the network ID. The prefix is used for routing IPv6 packets. |
| Interface ID | The rightmost bits of the IPv6 address used to uniquely identify a network card (interface) in a host. |
| Anycast | A unicast address that is assigned to more than one interface, typically interfaces belonging to different hosts. |
| Local Loopback | The local loopback address for the local host is 0:0:0:0:0:0:0:1 (also identified as ::1 or ::1/128). The local loopback address is not assigned to an interface. It can verify that the TCP/IP protocol stack is properly installed on the host. |
| Dual Stack | A dual stack configuration enables a host to communicate with IPv4 and IPv6 hosts; the IPv4 and IPv6 protocol stacks run concurrently on a host. |
| Tunneling | Tunneling allows IPv6 hosts or sites to communicate over the existing IPv4 infrastructure. A device encapsulates IPv6 packets within IPv4 packets for transmission across an IPv4 network, and then the IPv6 packets are de-encapsulated by another device at the other end. |
| Static Full Assignment | The entire 128-bit address and all other configuration information is statically assigned to the host. |
| Static Partial Assignment | The prefix is statically assigned. The interface ID is derived from the MAC address. |
| Stateless Autoconfiguration | Clients automatically generate the interface ID and learn the subnet prefix and default gateway through the Neighbor Discovery Protocol (NDP). |
| DHCPv6 | IPv6 uses an updated version of DHCP, DHCPv6. It operates in two modes, stateful and stateless. |
The addresses available under the current IPv4 addressing standard have been exhausted. In response to this situation, a new IP addressing system (IP version 6, or IPv6) has been developed. An IPv6 address is a 128-bit binary number. A sample IPv6 IP address looks like the following: 35BC:FA77:4898:DAFC:200C:FBBC:A007:8973.
Features of an IPv6 Address
The following list describes the features of an IPv6 address:
- It is made up of 32 hexadecimal numbers organized into 8 quartets.
- The quartets are separated by colons.
- Each quartet is represented as a hexadecimal number between 0 and FFFF. Each quartet represents 16 bits of data (FFFF = 1111 1111 1111 1111).
- Leading zeros can be omitted in each section. For example, the quartet 0284 could also be written as 284.
- An address with consecutive zeros can be expressed more concisely by
substituting a double colon for the group of zeros. For example:
- FEC0:0:0:0:78CD:1283:F398:23AB
- FEC0::78CD:1283:F398:23AB (concise form)
This is also called address compression. Address compression is when you take a fully-notated IPv6 address and remove empty octets from it, replacing them with a colon.
- If an address has more than one consecutive location where one or more
quartets are all zeros, only one location can be abbreviated. For example,
FEC2:0:0:0:78CA:0:0:23AB can be abbreviated as:
- FEC2::78CA:0:0:23AB
or - FEC2:0:0:0:78CA::23AB
but not - FEC2::78CA::23AB
- FEC2::78CA:0:0:23AB
- The 128-bit address contains two parts:
Component Description Prefix The first 64 bits are known as the prefix. - The prefix can be divided into various parts that identify things such as geographic region, the ISP, the network, and the subnet.
- The prefix length identifies the number of bits in the relevant portion of the prefix. To indicate the prefix length, add a slash (/) followed by the prefix length number. Full quartets with trailing 0s in the prefix address can be omitted (e.g., 2001:0DB8:4898:DAFC::/64).
- Because addresses are allocated based on physical location, the prefix generally identifies the location of the host. The 64-bit prefix is often referred to as the global routing prefix.
Interface ID The last 64 bits are known as the interface ID. This is the unique address assigned to an interface. - Addresses are assigned to interfaces (network connections), not to the host. Technically, the interface ID is not a host address.
- In most cases, individual interface IDs are not assigned by ISPs but are rather generated automatically or managed by site administrators.
- Interface IDs must be unique within a subnet, but they can be the same if they are on different subnets.
- On Ethernet networks, the interface ID can be automatically derived from the MAC address. Using the automatic host ID simplifies administration.
To ensure that the interface ID is unique for every host on the network, IPv6 uses the Extended Unique Identifier 64 (EUI-64) format. The following are some details of the EUI-64 format:
- Each host has a unique 48-bit hardware address called a
MAC address (also called the burned-in
address) that is assigned to each device by the vendor. The MAC
address is guaranteed to be unique through design. The EUI-64
format uses the unique MAC address by:
- Splitting the MAC address into 24-bit halves.
- Inserting 16 bits (represented by hex FFFE) between the
two halves.
For example, a host with a MAC address of 20-0C-FB-BC-A0-07 would start with the following EUI-64 interface ID: 200C:FBFF:FEBC:A007.
- To be complete, the EUI-64 format requires setting the
seventh bit in the first byte to binary 1 (reading from left
to right, this is the second hex value in the interface ID).
This bit is called the
universal/local (U/L) bit.
- When the U/L bit is set to 0, the MAC address is a burned-in MAC address.
- When the U/L bit is set to 1, the MAC address has been configured locally. EUI-64 requires the U/L bit to be set to 1.
- 200C:FBFF:FEBC:A007 (Incorrect interface ID, as the U/L bit is still set to 0)
- 220C:FBFF:FEBC:A007 (Correct interface ID)
IPv6 adds the following features not included in IPv4:
| Feature | Description |
| Auto-configuration | Because hardware IDs are used for node IDs, IPv6 nodes simply need to discover their network IDs. This can be done by communicating with a router. |
| Built-in Quality of Service | Built-in support for bandwidth reservations makes guaranteed data transfer rates possible. (Quality of service features are available as add-ons within an IPv4 environment but are not part of the native protocol.) |
| Built-in Security Features | IPv6 has built-in support for security protocols such as IPsec. (IPsec security features are available as add-ons within an IPv4 environment.) |
| Source Intelligent Routing | IPv6 nodes have the option to include addresses that determine part or all of the route a packet will take through the network. |
IPv6, assigns addresses to interfaces (network connections). All interfaces require an IPv6 address, and each interface can have more than one IPv6 address. IPv6 defines the following types of addresses:
| Address Type | Description | |
| Unicast |
Unicast addresses are assigned to a single interface for the
purpose of allowing one host to send and receive data. Packets sent
to a unicast address are delivered to the interface identified by
that address.
There are three types of unicast IPv6 addresses: |
|
| Link-local |
Link-local addresses (also known as local link
addresses) are only valid on the current subnet. Details include the
following:
Do not use link-local IPv6 addressing on routed networks. Routers never forward packets destined for link-local addresses to other subnets. |
|
| Unique local |
Unique local addresses are private addresses used for
communication within a site or between a limited number of sites. In
other words, unique local addressing is commonly used for network
communications that do not cross a public network; they are the
equivalent of private addressing in IPv4. Details include the
following:
The process for designing a network addressing scheme when using unique local addresses is similar to that used for global unicast addresses. The key difference is how the prefix is defined. Because the address range is not registered, a global routing prefix does not have to be requested from an ISP. Instead, each organization defines its own prefix. |
|
| Global unicast |
Global unicast addresses are assigned to individual interfaces
that are globally unique. All IPv6 addresses that aren't
specifically reserved for other purposes are defined as global
unicast addresses. The global routing prefix assigned to an
organization by an ISP is typically 48 bits long (/48), but it could
be as short as /32 or as long as /56, depending on the ISP. All
subnet IDs within the same organization must begin with the same
global routing prefix, but they must also be uniquely identified
using a different value in the subnet field.
Using this addressing scheme allows organizations to define a large number (216) of IPv6 subnets. When you design an IPv6 network, define separate IPv6 subnets by the following:
|
|
| Multicast |
Multicast addresses represent a dynamic group of hosts. Packets
sent to a multicast address are sent to all interfaces identified by
that address. If different multicast addresses are used for
different functions, only the devices that need to participate in a
particular function will respond to the multicast; devices that do
not need to participate in the function will ignore the multicast.
Details include the following:
There are no broadcast addresses in IPv6. IPv6 multicast addresses are used instead of broadcast addresses. |
|
| Anycast |
The anycast address is a unicast address that is assigned to
more than one interface, typically belonging to different hosts. An
anycast packet is routed to the nearest interface having that
address (based on routing protocol decisions). Details include the
following:
|
|
| Loopback | The local loopback address for the local host is 0:0:0:0:0:0:0:1 (also identified as ::1 or ::1/128). The local loopback address is not assigned to an interface. It can verify that the TCP/IP protocol stack is properly installed on the host. | |
IPv4 to IPv6 Migration
The worldwide transition from IPv4 to IPv6 will be a long process. Although IPv6 is not yet widely adopted, you can implement it if your systems support it. As the implementation of IPv6 proceeds, there will be times when compatibility with IPv4 will be necessary.
IPv6 Deployment Strategies
The following table lists various strategies for deploying IPv6.
| Method | Description | |
| Dual Stack | A dual stack configuration enables a host to communicate with IPv4 and IPv6 hosts; the IPv4 and IPv6 protocol stacks run concurrently on a host. IPv4 is used to communicate with IPv4 hosts, and IPv6 is used to communicate with IPv6 hosts. When dual stack is implemented on hosts, intermediate routers and switches must also run both protocol stacks. | |
| Tunneling |
Tunneling allows IPv6 hosts or sites to communicate over the
existing IPv4 infrastructure. A device encapsulates IPv6 packets
within IPv4 packets for transmission across an IPv4 network, and
then the IPv6 packets are de-encapsulated by another device at the
other end.
Tunneling solutions include the following: |
|
| Manually Configured tunnel |
In this configuration, tunnel endpoints are configured as
point-to-point connections between devices. Because of the time and
effort required for configuration, use manually configured tunnels
only when you have a small number of sites that need to connect
through the IPv4 internet or when you want to configure secure
site-to-site associations. Manual tunneling:
|
|
| 6-to-4 Tunneling |
With 6-to-4 tunneling, tunneling endpoints are configured
automatically between devices. Use 6-to-4 tunneling to dynamically
connect multiple sites through the IPv4 internet. Because of its
dynamic configuration, 6-to-4 tunneling is easier to administer than
manual tunneling. 6-to-4 tunneling:
|
|
| 4-to-6 Tunneling | 4-to-6 tunneling works in a manner similar to 6-to-4 tunneling. However, instead of tunneling IPv6 traffic through an IPv4 network, 4-to-6 tunnels IPv4 traffic through an IPv6 network by encapsulating IPv4 packets within IPv6 packets. | |
| Intra-site Automatic Tunnel Addressing Protocol (ISATAP) |
The intra-site automatic tunnel addressing protocol is a tunneling
method that provides IPv6 communication over a private IPv4 network.
ISATAP tunneling:
|
|
| Teredo Tunneling |
Teredo tunneling establishes a tunnel between individual hosts so they
can communicate through a private or public IPv4 network. Teredo
tunneling:
|
|
IPv6 Address Assignment
You can configure an IPv6 address with any of the methods in the following table.
IPv6 Configuration Methods
| Method | Description |
| Static Full Assignment | The entire 128-bit address and all other configuration information is statically assigned to the host. |
| Static Partial Assignment | The prefix is statically assigned. The interface ID is derived from the MAC address. |
| Stateless Autoconfiguration |
Clients automatically generate the interface ID and learn the subnet
prefix and default gateway through the Neighbor Discovery Protocol
(NDP). NDP uses the following messages for autoconfiguration:
NDP provides enough information for to address the client and for clients to learn the addresses of other clients on the network. However, it does not provide the client with DNS server information or any other IP configuration information besides the IP address and the default gateway. |
| DHCPv6 |
IPv6 uses an updated version of DHCP, DHCPv6. It operates in one of two
modes:
|
IPv6 Configuration Process
When a host starts up, it uses the following process to configure the IPv6 address for each interface:
- The host generates an IPv6 address using the link-local prefix (FE80::/10) and modifies the MAC address to get the interface ID. For example, if the MAC address is 20-0C-FB-BC-A0-07, the link-local address for the interface is FE80::220C:FBFF:FEBC:A007.
- The host sends a neighbor solicitation (NS) message addressed to its own
link-local address to see if the address it has chosen is already in use:
- If the address is in use, the other network host responds with a neighbor advertisement (NA) message. The process stops, and you must configure the host manually.
- If the address is not in use (no NA message is received), the process continues.
- The host waits for an RA message from a router to learn the prefix:
- If an RA message is not received, the host uses the multicast address FF02::2 to send an RS message addressed to all routers on the subnet.
- The router sends an RA message addressed to all interfaces on the subnet using the multicast address FF02::1.
- If no routers respond, the host attempts to use stateful DHCPv6 to receive configuration information.
- The RA message contains information that identifies how the IPv6 address
and other information should be configured. The following table shows
possible combinations:
Configuration Method Description Stateful Autoconfiguration Obtains the interface ID, subnet prefix, default gateway, and other configuration information from a DHCPv6 server.
The host sends a REQUEST message addressed to the multicast address FF02::1:2, requesting this information from the DHCPv6 server.
Stateless Autoconfiguration Sets the interface ID automatically.
Obtains the subnet prefix and default gateway from the RA message.
Obtains DNS and other configuration information from a DHCPv6 server.
The host sends out an INFORMATION-REQUEST message addressed to the multicast address FF02::1:2, requesting this information from the DHCPv6 server.
- If a manual address or stateful autoconfiguration is used, the host sends an NS message to make sure the address is not already in use. If stateless autoconfiguration is used, the NS message is unnecessary because the interface ID was verified in step 2.
IPv6 Address Management
A good way to manage IP addresses is to use IP address management (IPAM). IPAM allows you to plan, track, and manage IP addresses using integrated DHCP and DNS information. This allows administrators to keep a pool of assignable IP addresses up-to-date. IPAM tools are becoming more important for managing IPv6 networks because IPv6 networks have larger address pools, different subnetting techniques, and more complex 128-bit hexadecimal numbers.
IPAM can manage the following information:
- IP addresses in use
- The user an IP address is assigned to
- Free IP address space
- The size of subnets, who uses them, and how many subnets are in use
- IP address status (permanent vs. temporary)
- Default routers that the various network devices use
- The host name associated with each IP address
- The hardware associated with each IP address
Multicast
As you study this section, answer the following questions:
- How does multicast differ from unicast and broadcast?
- What is the IP address range reserved for multicast groups?
- What does a regular switch do when it receives a multicast frame?
- Which device would you configure to prevent multicast traffic from being sent to non-group members?
The key terms for this section include:
| Term | Definition |
| Unicast | Messages are sent to a specific host address. The sending device must know the IP address of all recipients and must create a separate packet for each destination device. |
| Broadcast | A single packet that, when sent, is processed by all hosts. Broadcast packets are not typically forwarded by routers, so broadcast traffic is limited to within a single subnet. |
| IGMP | The Internet Group Management Protocol (IGMP) is used to identify group members and to forward multicast packets on to the segments where group members reside. |
Multicasting creates logical groups of hosts—messages sent to the group are received by all group members. Multicasting is typically used for streaming video and audio applications, such as video conferencing.
Without multicasting, messages sent to a specific group only use the following:
| Method | Description |
| Unicast | Messages are sent to a specific host address. The sending device must know the IP address of all recipients, and must create a separate packet for each destination device. |
| Broadcast | A single packet is sent to the broadcast address and is processed by all hosts. All hosts, and not just group members, receive the packet. Broadcast packets are not typically forwarded by routers, so broadcast traffic is limited to within a single subnet. |
IGMP
The Internet Group Management Protocol (IGMP) is used to identify group members and to forward multicast packets on to the segments where group members reside. IGMP routers keep track of the attached subnets that have group members, using the following process:
- A router sends out a host membership query. This query is addressed to
the IP address 224.0.0.1.
- The address 224.0.0.1 is never assigned to a group because it is used for the query messages sent by routers.
- Hosts that are members of any groups respond with a list of the groups they belong to. Each group is identified with a multicast IP address in the range of 224.0.0.0 to 239.255.255.255.
- The router uses these responses to compile a list of the groups on the subnet that have group members. Routers do not keep track of individual hosts that are members of a group; they simply compile a list of groups on the subnet that have at least one member.
- When a host joins a new group, it automatically sends a join group message to the router. When the last host in a group leaves the group, it sends a leave group message to the router.
- The IGMP router reports to upstream routers that they have members of a
specific group.
- Upstream routers are the routers that exist between the router and the server that sends out the multicast data stream. They keep track of downstream routers that have group members.
Multicast Stream
The following process is used when sending a multicast stream:
- The sending server sends packets addressed to the multicast group.
- Routers receive the multicast packets and check their lists of group
members.
- If the router is connected to a subnet that has group members, or if the subnet includes a downstream router with group members, the multicast packet is sent on that subnet.
- If a subnet does not have any group members, the packet is not forwarded on that subnet.
- If a router does not have any subnets with group members, the packet is dropped and not forwarded.
- Each intermediary router performs the same tasks until the data stream eventually reaches the multicast client.
Additional Facts
Additional multicasting facts include:
- Frames that contain multicast traffic are sent to a special MAC address. The MAC address begins with 01-00-5E, with the last portion being a form of the IP multicast group address. A single multicast MAC address could be shared by up to 5 other IP multicast addresses.
- A regular switch that receives multicast traffic sends the traffic out all ports, because the destination MAC address will be an unknown address. This means that a host might see multicast traffic on its segment, even if it isn't a member of the group. However, hosts that are not members of the group will not process the frame because they will not associate the multicast MAC address with their own address.
- IGMP snooping on a switch allows the switch to control which ports get IGMP traffic for a specific group. With IGMP snooping, the switch identifies which ports include members of a specific multicast group. When a message is received for a group, the message is sent only to the ports that have a group member connected.
Troubleshooting IP Configuration Issues
As you study this section, answer the following questions:
- What does the /release switch do when used with ipconfig?
- How can you tell if a rogue DHCP server is active on your network?
- How do you know if a host is using APIPA?
In this section, you will learn to:
- Find information about IP configuration settings on Windows and Linux systems.
- Troubleshoot IP configuration problems.
The key terms for this section include:
| Term | Definition |
| APIPA | APIPA (Automatic Private IP Addressing) is the Windows function that provides DHCP autoconfiguration addressing. When the DHCP process fails, Windows will automatically assign an IP address from the private range of 169.254.0.1 to 169.254.255.254. Once the address has been assigned, the host uses Address Resolution Protocol (ARP) to verify that the chosen APIPA address is unique. |
| ipconfig | ipconfig is a command line tool used to control the network connections on Windows machines. |
| DHCP | Dynamic Host Configuration Protocol (DHCP) is a protocol used to centrally manage the distribution of IP addresses within a network. |
| DNS | DNS stands for Domain Name System. The main function of DNS is to translate domain names into IP Addresses, which computers can understand. |
This section helps you prepare for the following certification exam objectives:
| Exam | Objective |
| TestOut Network Pro |
3.4 Use network tools to discover network devices and resources. 5.2 Troubleshoot IP configuration issues to establish network communication. |
| CompTIA Network+ |
5.2 Given a scenario, use the appropriate tool.
5.5 Given a scenario, troubleshoot common network service issues.
|
IPconfig Utility
You can use ipconfig /all to troubleshoot IP configuration problems. The following table describes how the output for this command changes, based on how IP settings are configured and for specific problem situations:
| Condition | ipconfig /all Output |
| Static IP Configuration |
If the workstation is configured with static IP information, the following conditions will exist:
|
| DHCP Configuration |
If the workstation has received configuration information from a DHCP server, the following conditions will exist:
|
| Rogue DHCP Server |
A rogue DHCP server is an unauthorized DHCP server on the network. Symptoms of a rogue DHCP server include:
When you have a rogue DHCP server on the network, some hosts will likely receive configuration information from the correct DHCP server and others from the rogue DHCP server. |
| Incorrectly Configured DHCP Server | Your DHCP server can send out various IP configuration values, like the IP address and mask. If network hosts are configured with incorrect IP values (such as incorrect default gateway or DNS server addresses), first verify that the workstations are contacting the correct DHCP server. If the correct server is being used, go to the DHCP server to verify that it is sending out correct configuration information. |
| APIPA Configuration |
If the workstation used APIPA to set configuration information, the following conditions will exist:
When APIPA is used, the workstation sets its own IP address and mask. It does not automatically configure default gateway or DNS server values. When APIPA is being used:
|
| Alternate Configuration |
If the workstation has been configured using an alternate configuration, the following conditions will exist:
|
| Duplicate MAC Addresses |
The MAC address is a 12-digit hexadecimal number (48 bits). This address is unique, so you should not have duplicate
addresses on your network. However, it is possible for two hosts to have the same MAC address, due to spoofing, a mistake
during manufacturing, or if users choose a self-assigned address instead of the vendor-assigned hardware address. This
last one is more common when using main frame systems that communicate via MAC addresses rather than protocol addresses
(IP addresses).
An Ethernet switch keeps a table of which MAC addresses are attached to which ports. It uses the source address of frames it receives during the normal operation of the network to make the table. When the switch receives a frame, the source MAC is read and compared with the current table, and then added alongside whichever switch port it was received on. Therefore, if there are two hosts with the same MAC address, then the switch will update it's MAC table every time it receives a frame from either host. Reaching either host will be inconsistent and cause other problems as well. |
Exhausted DHCP scope means that all of the addresses within the DHCP scope were depleted. As a consequence, a legitimate user is denied an IP address requested through DHCP and is not able to access the network. This situation is usually caused by an attack called DHCP starvation. This attack might be a DoS mechanism or be used together with a malicious rogue server attack to redirect traffic to a malicious computer ready to intercept traffic.
If the workstation has received configuration information from the wrong DHCP server or has configured itself using APIPA, you may need to contact the DHCP server again once the DHCP problems have been resolved. Use the following commands:
- ipconfig /release to stop using the current dynamic IP configuration parameters.
- ipconfig /renew to retry the DHCP server request process to obtain IP configuration parameters.
To display the TCP/IP configuration on a Linux computer, use the ifconfig command.
Troubleshoot IP Communication
As you study this section, answer the following questions:
- What is the difference between netstat and arp?
- If a ping test fails, what should you do?
- What information does tracert provide?
- What does TCPdump do?
In this section, you will learn to:
- Use ping and tracert.
- Use arp and netstat.
- Use tcpdump.
- Explore network communications.
The key terms for this section include:
| Term | Definition |
| ping | ping sends an ICMP echo request/reply packet to a remote host. A response from the remote host indicates that both hosts are correctly configured and a connection exists between them. |
| Address Resolution Protocol (ARP) |
Hosts use ARP to discover the MAC address of a device from its IP address. |
| tcpdump | tcpdump is a packet analyzer that runs in a command line utility. It allows the user to view TCP/IP and other packets as they are transmitted and received over a computer's network. |
This section helps you prepare for the following certification exam objectives:
| Exam | Objective |
| TestOut Network Pro |
3.4 Use network tools to discover network devices and resources. 5.2 Troubleshoot IP configuration issues to establish network communication. |
| CompTIA Network+ |
1.3 Explain the concepts and characteristics of routing and switching.
5.2 Given a scenario, use the appropriate tool.
5.5 Given a scenario, troubleshoot common network service issues.
|
As part of the troubleshooting process, you need to identify the scope of the problem so you can take the proper actions to correct the problem.
In this scenario, Workstation A can't communicate with Workstation C.
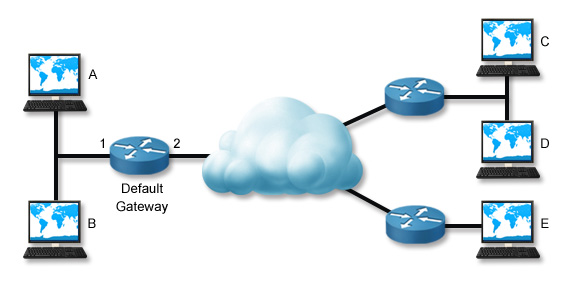
Troubleshooting Process
The following table lists several tasks you can perform to troubleshoot the reported connectivity problem. These steps trace the problem backward from the remote host to the local host. Depending on the situation, you might be able to troubleshoot the problem more efficiently by skipping some tests or changing the order in which you perform them (you might even complete them in reverse order).
| Task | Description |
| Ping Host C |
Often, the best way to start troubleshooting a problem is to ping the host you are trying to contact. This verifies the
reported problem. If the ping is successful, the problem is not related to network connectivity. Check other problems,
such as name resolution or service access.
If you have access to another computer, try pinging the destination host from that computer. If the ping is successful, skip the remaining tasks and troubleshoot the local host configuration or physical connection. |
| Ping Host D | If you cannot contact a specific remote host, try pinging another host in the same remote network. If the ping is successful, then the problem is with the remote host (for example, a misconfiguration, broken link, or unavailable host). |
| Ping Host E | If you cannot contact any host in the remote network, try pinging hosts on other remote networks (you might try several other networks). If the pings are successful or if you can contact some remote networks and not others, then the problem is with the routing path between your network and the specific remote network. Use the traceroute/tracert commands to check the path to the problem network. |
| Ping the Default Gateway | If you cannot contact any remote network, ping the default gateway router. If the ping is successful but you still cannot contact any remote host, have the router administrator verify the router configuration. Check for broken links to the remote network, interfaces that have been shut down, and access control lists or other controls that might be blocking traffic. |
| Ping Host B | If you cannot contact the default gateway router, ping other hosts on the local network. If the pings are successful, check the default gateway router. |
| Troubleshoot the Local Host Connection or Configuration |
If you cannot communicate with any host on the local network, then the problem is likely with the local host or its
connection to the network. Troubleshoot by doing the following:
|
You can use the route command on the router to view directly connected routes that have been set up. You can also use it on the default gateway of the local subnet and verify that the router has a route to the remote subnet. Another use of the route command is to view the routing table; this helps you see what networks the router knows about. In addition, the route command can be used to display additional networking information (not provided by ifconfig).
One special ping test you can perform is pinging the local host. By doing this, you are verifying that TCP/IP is correctly installed and configured on the local host. In essence, you are finding out if the workstation can communicate with itself. To ping the local host, use the following command:
ping 127.0.0.1
If this test fails, check to make sure TCP/IP is correctly configured on the system.
This test does not check physical connectivity. The ping can succeed even if the host is disconnected from the network.
ARP and netstat
The following table lists several commands that you can use on a Windows system to gather information about network connections.
| Tool | Option(s) |
| arp | arp -a shows the IP address-to-MAC address mapping table (the address cache). |
| netstat | netstat shows the active connections. |
| netstat -a shows detailed information for active connections. | |
| netstat -r or route print shows the routing table of the local host. | |
| netstat -s shows TCP/IP statistics. | |
| arp table | arp tables allow a system to build frames targeting remote MAC addresses. |
Local computers have a cache of recently used IP addresses and their corresponding MAC addresses. When a computer needs to contact another computer on its own subnet, it first checks its cache for an entry of the IP address. If the entry is found, the corresponding MAC address is used to communicate with the destination computer. The cache can cause problems if the MAC address for a computer has recently changed (for example, if the network interface card has been replaced). To correct a problem, use the netsh command to clear the ARP cache.
arp -a shows the IP address-to-MAC address mapping table (the address cache).
A sample output looks like this:
|
```Interface: 192.168.1.141 on Interface 0x1000003
Internet Address Physical Address Type
192.168.1.1 00-40-10-18-7c-ed dynamic
192.168.1.20 00-0e-0c-4e-e0-b2 dynamic
192.168.1.21 00-0e-0c-4e-e1-fe dynamic
192.168.1.22 00-0e-0c-4e-df-c6 dynamic
192.168.1.23 00-d0-b7-b7-c2-af dynamic
192.168.1.26 00-0e-0c-4e-e9-d6 dynamic
```
</table>
Occasionally, the ARP table will have stale entries. This happens when:
If this is the case, when the local computer consults its cache for ARP information, the information will be incorrect, and the computer will be unable to contact the remote host. To correct the problem, use the arp -d * command to delete the cache. This causes the computer to use ARP to rediscover the information. netstat shows the active connections. A sample output looks like this: ``` Active Connections Proto Local Address Foreign Address State TCP wrk1:microsoft-ds wrk1.westsim.local:1342 ESTABLISHED TCP wrk1:1342 wrk1.westsim.local:microsoft-ds ESTABLISHED TCP wrk1:1088 srv1.westsim.local:1026 ESTABLISHED TCP wrk1:1096 srv1.westsim.local:1865 ESTABLISHED TCP wrk1:1232 srv1.westsim.local:microsoft-ds ESTABLISHED ```netstat -a shows detailed information for active connections. A sample output looks like this:
|